
Google Professional Cloud DevOps Engineer
Get started today
Ultimate access to all questions.
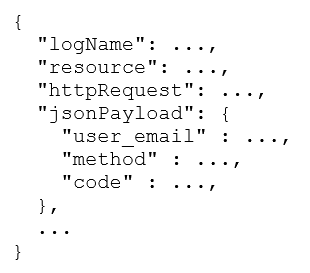
Your company operates an e-commerce business on Google Cloud Platform (GCP). The payment processing application generates structured JSON logs with the schema.
The jsonPayload.user_email field contains personally identifiable information (PII), and the security team requires that only they have access to this field. The engineering team must retain access to non-PII log data for operational purposes. How should you configure GCP to prevent the engineering team from accessing PII while allowing the security team exclusive access to the user_email field?
Your company operates an e-commerce business on Google Cloud Platform (GCP). The payment processing application generates structured JSON logs with the schema.
The jsonPayload.user_email field contains personally identifiable information (PII), and the security team requires that only they have access to this field. The engineering team must retain access to non-PII log data for operational purposes. How should you configure GCP to prevent the engineering team from accessing PII while allowing the security team exclusive access to the user_email field?
Exam-Like
A
Apply the conditional role binding resource.name.extract("locations/global/buckets/{bucket}/") == "_Default" to the _Default bucket.
14.3%
B
Comments
Loading comments...